Discover best practices for secure IT outsourcing with CMC Global. Learn how to protect your business from data breaches, ensure compliance with regulations like CCPA, VCDPA, and CPA, and choose the right partner with robust security measures and expertise.
The Growing Importance of Secure IT Outsourcing
With 83% of organizations experiencing data breaches and 60% of small businesses failing after cyberattacks, security in IT outsourcing is critical. Third-party vulnerabilities account for over 15% of breaches, while tightening U.S. regulations like CCPA, VCDPA, and CPA impose strict compliance demands.
To stay protected, IT vendors must have a strong security foundation with encryption, compliance frameworks (NIST, ISO 27001), and continuous monitoring. Choosing a partner with robust security measures and regulatory expertise is key to mitigating risks.
This guide explores best practices for secure IT outsourcing and how CMC Global can safeguard your digital legacy.
Key Data Privacy Laws Impacting IT Procurement In The U.S
California Consumer Privacy Act (CCPA) & California Privacy Rights Act (CPRA)
California has led the way in data privacy with the CCPA, granting consumers rights over their data, including access, deletion, and opt-out options for data sales. The CPRA adds stricter rules on data sharing and enforces compliance through the California Privacy Protection Agency (CPPA).
Key CCPA/CPRA Requirements:
- Businesses must disclose data collection and usage practices.
- Consumers have the right to request access, correction, and deletion of their data.
- Companies must implement robust security measures to protect personal information.
Virginia Consumer Data Protection Act (VCDPA)
The VCDPA, effective from January 1, 2023, applies to businesses processing data of at least 100,000 consumers or deriving 50% of revenue from selling data.
Key VCDPA Provisions:
- Requires businesses to conduct data protection assessments.
- Mandates opt-in consent for processing sensitive data.
Colorado Privacy Act (CPA)
The CPA, which took effect on July 1, 2023, applies to businesses that process data of 100,000 consumers annually or derive revenue from the sale of personal data.
Key CPA Compliance Measures:
- Grants consumers rights to data access, correction, and deletion
- Clear consent is required for sensitive data processing and regular compliance assessments.
How CMC Global Ensures Secure IT Outsourcing
To help businesses safeguard their digital assets while outsourcing IT services, CMC Global implements a security-first approach that ensures compliance and resilience against cyber threats.
Privacy-Centric Data Processing
CMC Global follows Privacy by Design principles, embedding security measures at every stage of data processing. This includes:
- Data Minimization – Collecting only essential data to reduce exposure risks.
- Anonymization & Pseudonymization – Replacing personal identifiers with non-identifiable data.
- Consumer Rights Management – Providing tools to facilitate access, correction, and deletion requests.
Industries like BFSI and healthcare must comply with strict regulations (e.g., GDPR, CCPA, HIPAA). To mitigate risks, companies should implement dummy data and anonymization techniques, replacing real customer information with non-identifiable data for testing and development. CMC Global employs advanced anonymization to minimize exposure risks while maintaining operational efficiency.
Compliance-Driven Security Practices
CMC Global builds a solid foundation of security by adhering to the NIST Cybersecurity Framework (CSF 2.0) —the leading U.S. standard for cybersecurity resilience. With deep expertise in NIST-driven security models, Vietnamese IT professionals deliver secure, compliant outsourcing solutions that meet global expectations.
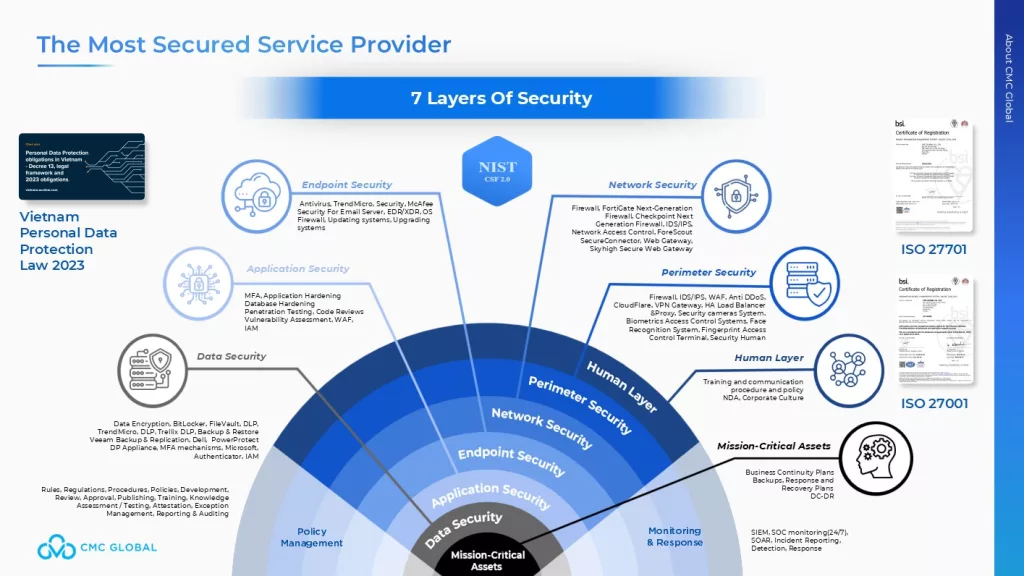
By integrating ISO 27001 with NIST principles, CMC Global establishes a robust security framework, including:
- Data Processing Agreements (DPAs): Ensuring compliance with U.S. regulations in outsourcing engagements.
- AES-256 Encryption: Protecting data at rest and in transit to prevent breaches.
- Multi-Factor Authentication (MFA) & Role-Based Access Control (RBAC): Strengthening access security and minimizing insider threats.
- Continuous Security Monitoring: Using AI-powered threat detection and Security Information & Event Management (SIEM) to identify and mitigate risks in real time.
Third-Party Risk Management & Secure Infrastructure
Outsourcing introduces third-party risks, making it essential to evaluate security protocols. CMC Global mitigates risks through:
- Vendor risk assessments before outsourcing engagements.
- Regular audits to verify compliance with U.S. data privacy laws.
- GDPR- and CCPA-compliant data storage solutions with disaster recovery plans.
Building a Secure IT Outsourcing Strategy

Organizations looking to safeguard their digital legacy must adopt a security-driven outsourcing model. This includes:
- Embedding security into DevOps (DevSecOps) to integrate security measures throughout development.
- Continuous monitoring and threat detection to proactively address security risks.
- Regular compliance updates and employee training to stay ahead of evolving regulations.
Future-Proof Your Secured IT Outsourcing Strategy
The evolving regulatory landscape and increasing cybersecurity threats make it essential for businesses to take a proactive approach to IT outsourcing security. Partnering with a security-focused IT provider like CMC Global ensures businesses remain compliant, resilient, and future-ready.
Connect with CMC Global today to learn how we can help you secure your IT outsourcing strategy and safeguard your digital legacy.




