In today’s digital age, businesses are increasingly reliant on their networks to stay connected and operate efficiently. However, networks are also vulnerable to attack, which can lead to data breaches, financial losses, and reputational damage.
That’s why it’s so important for businesses to have their networks regularly tested for security vulnerabilities. In this blog, CMC Global will delve into Network Security Testing, and how it is essential for the wellbeing of your business.
What is security testing?
Security testing is the process of evaluating the security of a system or application to identify and fix vulnerabilities that could be exploited by attackers. It is an essential part of any organization’s security posture, as it helps to ensure that systems and applications are protected from unauthorized access, modification, or destruction.
Why Security Testing is Important?
The main goal of Security Testing is to identify the threats in the system and measure its potential vulnerabilities, so the threats can be encountered, and the system does not stop functioning or cannot be exploited. It also helps in detecting all possible security risks in the system and helps developers to fix the problems through coding.
Types of Security Testing
There are many different types of security testing, each with its own specific focus. Some of the most common types of security testing include:

- Vulnerability Scanning – involves the use of an automated software tool to scan systems against predetermined vulnerabilities.
- Risk Assessment – consists of an analysis of security risks in the application, software or network. Once identified, they are classified as low, medium, high, or critical and mitigation measures can be enacted based on priority.
- Security Scanning – can be done with manual or automated testing and serves as a means for locating network or system weaknesses
- Penetration Testing – stimulates an attack from a malicious party or hacker and helps to clearly identify critical vulnerabilities in the system, software, or application
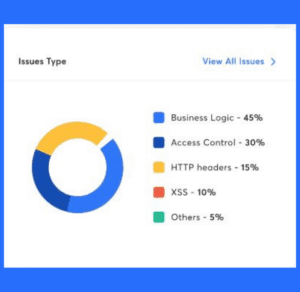
- Security Auditing – an internal inspection of all the operating systems and applications with the intent of finding security flaws. The results from the audit can be passed to the applicable teams for follow up and correction.
- Ethical Hacking – hired experts attempt to hack into a system or network with the goal of exposing flaws and gaps in the existing security measures.
- Posture Assessment – a combination of ethical hacking, security scanning, and risk assessments to give a snapshot of the overall security within the organization
What is Network Security Testing?
Network security testing is the process of analyzing and testing your network to identify bugs and performance issues, evaluate large network changes, and measure network performance. It is similar to software testing, but often has to happen in a production environment. After the configuration change a network infrastructure was made to identify and fix vulnerabilities that could be exploited by attackers.

Here’s what it involves:
The few types of network securities are discussed below:
- Access Control
- Antivirus and Anti-Malware Software
- Cloud Security
- Email Security
- Firewalls
- Application Security
- Intrusion Prevention System (IPS)
1. Access Control
Not every person should have a complete allowance for accessibility to the network or its data. One way to examine this is by going through each personnel’s details. This is done through Network Access Control which ensures that only a handful of authorized personnel must be able to work with the allowed number of resources.
2. Antivirus and Anti-malware Software: This type of network security ensures that any malicious software does not enter the network and jeopardize the security of the data. Malicious software like Viruses, Trojans, and Worms is handled by the same. This ensures that not only the entry of the malware is protected but also that the system is well-equipped to fight once it has entered.
3.Cloud Security
Now a day, a lot of many organizations are joining hands with cloud technology where a large amount of important data is stored over the internet. This is very vulnerable to the malpractices that few unauthorized dealers might pertain to. This data must be protected, and it should be ensured that this protection is not jeopardized by anything. Many businesses embrace SaaS applications for providing some of their employees the allowance of accessing the data stored in the cloud. This type of security ensures creating gaps in the visibility of the data.
4. Email Security
Email Security depicts the services and products designed to protect the Email Account and its contents safe from external threats. For Example, you generally see, fraud emails are automatically sent to the Spam folder. because most email service providers have built-in features to protect the content.
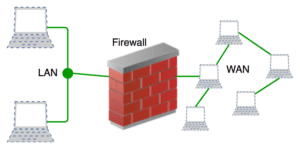
5. Firewalls
A firewall is a network security device, either hardware or software-based, which monitors all incoming and outgoing traffic and based on a defined set of security rules accepts, rejects, or drops that specific traffic. Before Firewalls, network security was performed by Access Control Lists (ACLs) residing on routers.
6. Application Security
Application security denotes the security precautionary measures utilized at the application level to prevent the stealing or capturing of data or code inside the application. It also includes the security measurements made during the advancement and design of applications, as well as techniques and methods for protecting the applications whenever.
7. Intrusion Prevention System (IPS)
An intrusion Prevention System is also known as Intrusion Detection and Prevention System. It is a network security application that monitors network or system activities for malicious activity. The major functions of intrusion prevention systems are to identify malicious activity, collect information about this activity, report it, and attempt to block or stop it.
What are the business outcomes of Network Security Testing?
Network Security Testing offers several concrete advantages for your business, offering a genuine ROI and long term advantages:
- Cost Savings: The average expense of a security breach can reach $4-5 million. Regular security tests help you avoid these substantial financial losses.
- Protecting All Stakeholders: By securing your network, you not only safeguard your business but also shield partners, third parties, and stakeholders, contributing to a secure digital environment.
- Business Continuity: Robust security measures significantly reduce the risk of network downtime, ensuring uninterrupted business operations.
- Regulatory Compliance: Network Security Testing makes it easier to comply with industry regulations, ensuring that your organization adheres to necessary standards.
- Building Trust: Prioritizing data protection instills confidence in customers and clients, strengthening your reputation and relationships in the business community.
How to Test Network Security
Network security testing involves mimicking real-world attack scenarios to evaluate the robustness of your defenses. It typically follows these steps:
- Planning: Define the scope, objectives, and methodologies for testing. Identify potential vulnerabilities.
- Scanning: Automated tools are used to scan the network for weaknesses, open ports, and potential vulnerabilities.
- Enumeration: This phase involves actively probing the network to gather information about the target, such as IP addresses and system details.
- Exploitation: Ethical hackers attempt to exploit vulnerabilities to gain unauthorized access. This step helps identify weaknesses that need immediate attention.
- Reporting: A detailed report is generated, highlighting the vulnerabilities discovered, their potential impact, and recommended remediation steps.
Test Scenarios for Network Security Examples
- Sample Test scenarios to give you a glimpse of security test cases:
- Scanning all network devices, such as routers and switches, for open ports or misconfigurations.
- Assessing the firewall rules to ensure they permit only authorized traffic.
- Evaluating intrusion detection and prevention systems for their ability to detect and block malicious activities.
- Testing the network for susceptibility to Distributed Denial of Service (DDoS) attacks.
- Verifying that sensitive customer data is transmitted securely through encrypted channels.
Conclusion
Network Security Testing is not just a precautionary measure; it’s an essential practice for safeguarding your business in today’s digital landscape. The benefits are clear: cost savings, comprehensive stakeholder protection, seamless business continuity, regulatory compliance, and enhanced trust among your customers and clients.
With over 30 years of experience, CMC Global is your trusted partner in safeguarding your network. Our 35+ business partners and 160+ ISTQB Foundation Certified Testers, along with 50+ ISTQB Advanced Certified Testers, vouch for our commitment to ensuring the highest standards of security. Contact us today for top-tier Security Testing services. Your business and stakeholders deserve nothing less than the best.