According to the 2025 Stack Overflow Developer Survey , 84% of respondents are using or planning to use AI tools in their development process, an increase over last year (76% in 2024). AI-powered tools like GitHub Copilot, ChatGPT, and Claude are revolutionizing how we code, test, and design. Features that once took weeks are now prototyped in days. The competitive advantage is undeniable.
But this breakneck speed has a dark side. Are we inadvertently building security vulnerabilities as fast as we’re building features? Many companies are trapped in a dilemma: lock down AI and fall behind or embrace it blindly and hope for the best.
Why Traditional Security Can’t Keep Up

Old-school security models are crumbling under the AI onslaught. Manual code reviews can’t scale to inspect AI-generated code that pours out by the second. The inherent “black box” nature of many models makes it difficult to understand why a code suggestion was made, obscuring logic flaws and biases.
Furthermore, AI introduces novel attack vectors:
- Prompt Injection: Manipulating the AI to output malicious code.
- Data Leakage: Developers accidentally feeding sensitive IP or customer data into public AI models.
- Supply Chain Risks: Inheriting vulnerabilities from the underlying AI models and platforms you depend on.
A Veracode report reveals that 45% of AI-generated code samples in a study were found to contain security vulnerabilities, including common issues like SQL injection and cross-site scripting.
Ignoring these risks isn’t just a technical misstep; it’s a compliance nightmare amidst evolving US regulations like the NIST AI Risk Management Framework and the White House Executive Order on AI.
The Core Principle: Shift-Left, Powered by AI
The solution is to fight fire with fire. The only way to secure AI-powered development at scale is to use AI-powered security tools. We must shift-left: integrating security directly into the earliest stages of the development process, creating a seamless, automated feedback loop for developers.
The 4-Layer AI Security Shield

This practical framework allows you to move fast without breaking things.
Layer 1: Policy & Education (The Human Firewall)
Technology is useless without governance. Start by creating a clear Acceptable Use Policy (AUP) that defines which AI tools are approved, for what purposes, and critically: what data classifications are strictly off-limits. Follow this with mandatory training for all developers on secure prompting techniques and AI-specific risks. Designate an “AI Security Champion” to own this initiative.
Layer 2: Tooling & Automation (The Technical Enforcer)
This is where you automate your policies.
- In the IDE: Use security plugins that scan AI-generated code suggestions in real-time, warning developers of vulnerabilities as they write.
- In the Pipeline: Integrate SAST (Static Application Security Testing) and SCA (Software Composition Analysis) tools into your CI/CD pipeline that are calibrated for AI-generated code. Every pull request must trigger an automated scan.
- AI-Specific Scanners: Employ emerging tools designed to detect prompt injection attempts and data leakage patterns before code is ever committed.
Layer 3: Process & Governance (The Guardrails)
Tools need processes to be effective.
- AI-Augmented Reviews: Use AI to summarize changes and flag potential security issues for human reviewers, making their job faster and more effective, not slower.
- Proactive Red Teaming: Don’t wait for an incident. Proactively test your AI applications with scenarios designed to exploit their unique weaknesses.
- Maintain Audit Trails: Keep logs of which models were used, the prompts given, and the code generated. This is non-negotiable for debugging, compliance, and incident response.
Layer 4: Culture & Iteration (The Growth Engine)
Finally, foster a culture where security enables innovation.
- Conduct blameless post-mortems to improve systems, not assign fault.
- Create feedback loops to continuously refine your tools and policies based on what you learn.
- Celebrate successes when developers identify and mitigate risks, reinforcing that security is a shared responsibility and a key value.
Secure Innovation is the Only Kind That Lasts
Building quickly is impressive. Building quickly and securely is how you build a legacy. By embedding this multi-layered shield into your development DNA, you move beyond fear and hesitation. You create a environment where developers can harness the full power of AI with confidence, knowing they have the guardrails to protect the company.
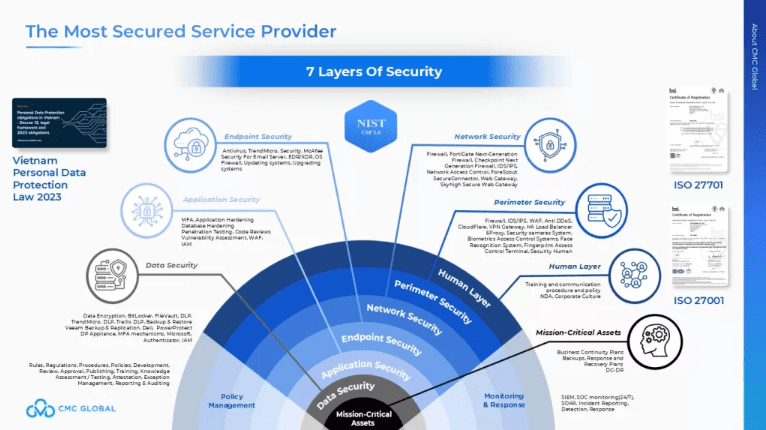
Businesses partnering with CMC Global benefit from a security-first approach that ensures compliance with industry standards. Through expert consulting services, CMC Global helps businesses navigate cybersecurity regulations like ISO 27001, ISO 27701, NIST CSF 2.0 with 7 layers of security: Human layer, Perimeter security, Network security, Endpoint security, Application security, Data security, Mission-critical assets.
Additionally, CMC Global fosters a highly skilled cybersecurity team, encouraging professionals to obtain top industry certifications such as Certified Information Systems Auditor (CISA), Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and Offensive Security Certified Professional (OSCP).
This commitment to compliance and expertise strengthens businesses’ security posture, mitigating risks and ensuring regulatory alignment.
Contact us today to learn more about how CMC Global can support your cybersecurity strategy!




