Imagine your company’s digital fortress is impenetrable. Your firewalls are robust, your employees are vigilant, and your data is encrypted. Yet, a devastating breach occurs, not through your main gates, but through a forgotten side entrance used by a third-party vendor. This is the stark reality of modern business. This makes proactive Third-Party Risk Management (TPRM) not just a compliance exercise, but a critical business imperative for survival and trust.
Understanding the Scope of Third-Party Risk
At its core, TPRM is the strategic process of identifying, assessing, and mitigating risks arising from your relationships with suppliers, vendors, and partners. It moves far beyond the perfunctory vendor questionnaire. The stakes are immense and multifaceted. A vulnerability in a vendor’s system can directly lead to a catastrophic data breach, exposing sensitive customer information and intellectual property.
Furthermore, a vendor’s non-compliance with regulations like GDPR, HIPAA, or PCI-DSS can result in massive fines that land squarely at your doorstep, even if the oversight was theirs. Beyond cybersecurity and compliance, third-party failures can cause crippling operational disruptions and inflict lasting reputational damage, eroding the hard-earned trust of your customers.
The Four Pillars of a Resilient TPRM Program
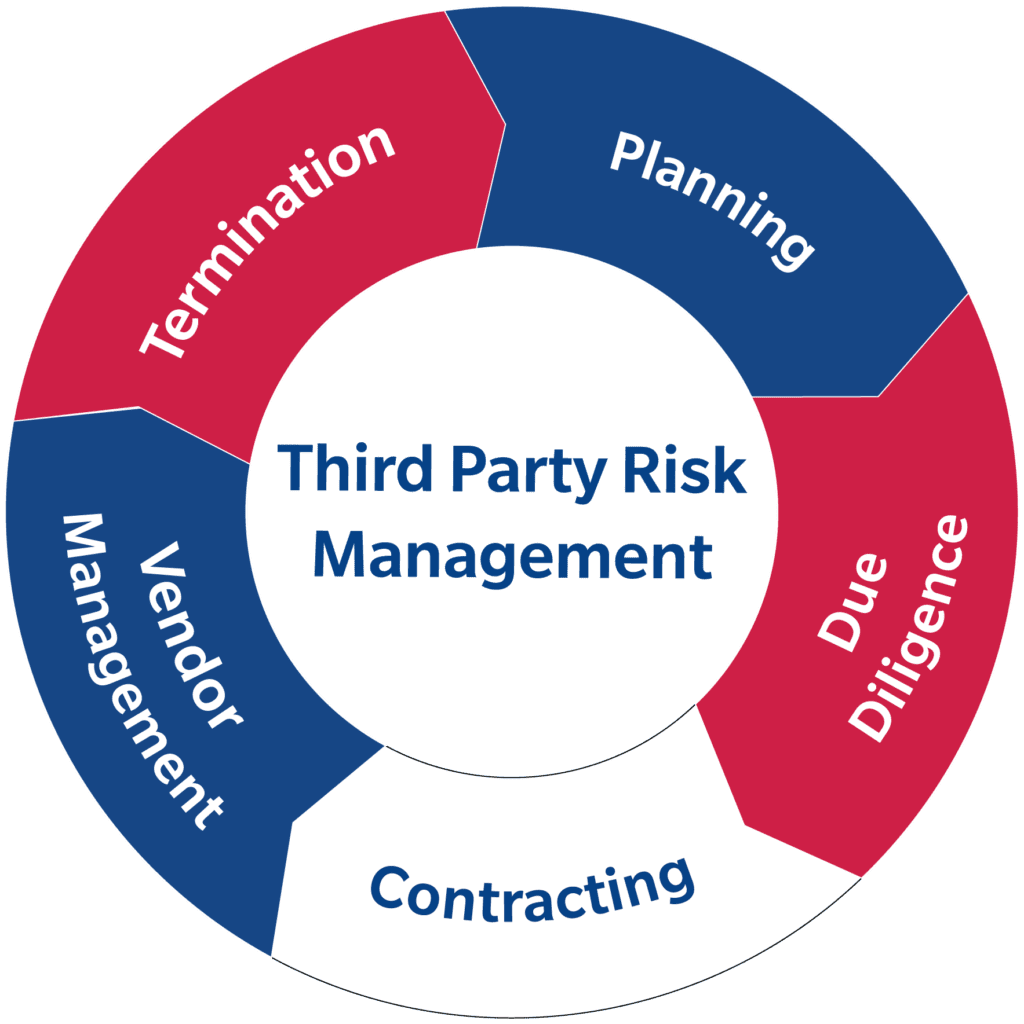
Building a robust TPRM framework is not a one-time project but an ongoing lifecycle, built upon four essential pillars.
The first pillar is Thorough Planning & Pre-Contract Due Diligence. This begins with intelligent vendor tiering, categorizing your partners based on the level of risk they introduce. A cloud provider storing sensitive personal data is inherently high-risk, while an office supply vendor is not.
For those high-risk relationships, due diligence must involve comprehensive assessments, leveraging standardized questionnaires, demanding proof of certifications like SOC 2 or ISO 27001, and, for the most critical partners, considering on-site audits.
Once a vendor passes initial scrutiny, the second pillar, Contractual Safeguards, comes into play. This is where you legally encode your security expectations. Key clauses must include the right to audit the vendor’s security practices, mandatory breach notification within a strict timeframe, clear data security requirements, and detailed liability provisions. A well-negotiated contract is your first and best line of defense.
However, the work does not stop at the signing ceremony. The third and most often neglected pillar is Continuous Monitoring and Ongoing Management. Vendor risk is dynamic; a secure company today could be compromised tomorrow. Effective TPRM requires constant vigilance through automated security rating platforms that provide real-time insights into a vendor’s security posture, supplemented by regular performance reviews and staying abreast of any vendor-related news concerning financial health or security incidents.
Finally, a complete program must account for the end of the relationship. The fourth pillar, Secure Offboarding and Termination, ensures that upon contract conclusion, all access rights are revoked, and your data is either completely destroyed or returned in a secure manner, preventing any lingering exposure.

Implementing this lifecycle is fraught with challenges. Organizations often feel overwhelmed by the sheer volume of vendors in their portfolio. The key is to start not with the easiest vendors, but with the most critical ones. By tiering your vendors, you focus precious resources where they matter most.
Another frequent hurdle is vendor pushback to lengthy questionnaires. You can overcome this by leveraging standardized forms and accepting existing audit reports, thereby reducing the assessment burden on them. Perhaps the most significant challenge is a simple lack of in-house expertise and bandwidth to interpret assessment results and manage the entire program effectively. This is where the strategic value of a specialized partner becomes undeniable.
The Strategic Advantage of a Specialized TPRM Partner
Building and maintaining a world-class TPRM program demands significant resources, dedicated personnel, sophisticated technology, and deep expertise that many organizations simply cannot afford to develop internally. Partnering with a specialized firm transforms this operational burden into a strategic advantage. It allows you to scale your efforts effortlessly, managing hundreds or thousands of vendors without a corresponding increase in headcount. You gain immediate access to expert analysts who can interpret security findings and provide actionable recommendations, not just raw data.
Furthermore, you leverage state-of-the-art technology platforms for continuous monitoring and automated alerts, all without a major capital investment. This partnership enables a shift from a reactive, checkbox-compliance model to a proactive, intelligence-driven security posture.
CMC Global: Your Trusted Partner in Building Resilience
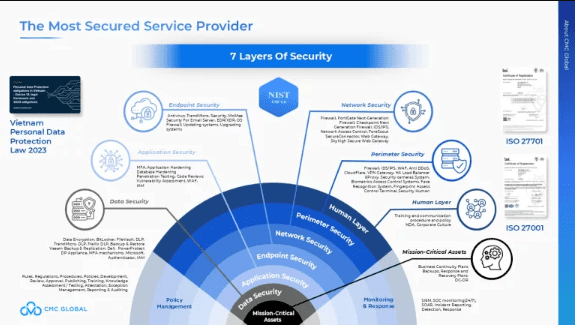
Businesses partnering with CMC Global benefit from a security-first approach that ensures compliance with industry standards. Through expert consulting services, CMC Global helps businesses navigate cybersecurity regulations like ISO 27001, ISO 27701, NIST CSF 2.0 with 7 layers of security: Human layer, Perimeter security, Network security, Endpoint security, Application security, Data security, Mission-critical assets.
Additionally, CMC Global fosters a highly skilled cybersecurity team, encouraging professionals to obtain top industry certifications such as Certified Information Systems Auditor (CISA), Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and Offensive Security Certified Professional (OSCP).
This commitment to compliance and expertise strengthens businesses’ security posture, mitigating risks and ensuring regulatory alignment.
Ready to transform your vendor risk from a weakness into a demonstrated strength?
Contact CMC Global today for a personalized consultation and discover how our expertise can help you build a more secure, compliant, and resilient future.




