The role of a CISO is no longer just about defending a perimeter. It’s about architecting resilience. With sophisticated threats targeting every vector: from cloud misconfigurations to sophisticated phishing campaigns, reliance on any single solution creates unacceptable risk. The answer isn’t a newer, bigger wall; it’s a smarter, layered blueprint.
This strategy, defense-in-depth, remains the cornerstone of effective security. It operates on a core principle: assume a breach will occur and ensure that no single point of failure can compromise the entire organization. For a modern CISO, this translates into a deliberate, seven-layer framework designed to protect, detect, and respond. Let’s deconstruct it.
Building Your Defense: The 7-Layer Security Framework
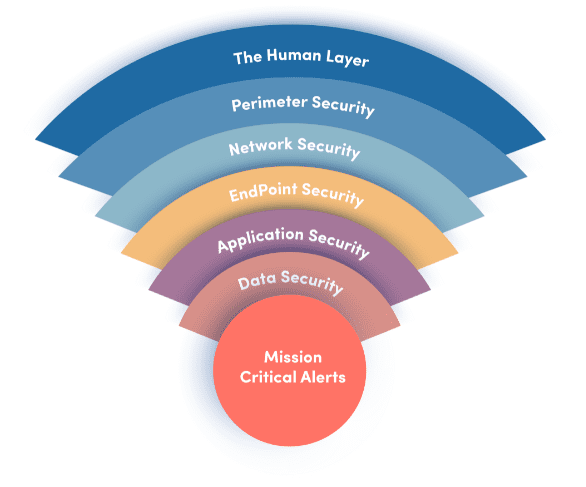
#1 The Human Firewall: Your First Line of Defense
The Verizon 2024 Data Breach Investigations Report (DBIR) found that the human element is involved in 68% of breaches. Of those, 80-95% are initiated by a phishing attack.
Technology is futile without informed users. This layer addresses the most common attack vector: people. Continuous, engaging security awareness training transforms your workforce from a vulnerability into a proactive sensor network. Simulated phishing exercises and clear reporting procedures ensure that when a clever email slips through, an employee becomes your first alert, not the first victim.
#2 Perimeter Security: The Digital Gate
While the traditional network edge has blurred, controlling traffic flow remains essential. Next-Generation Firewalls (NGFWs) and secure web gateways act as intelligent gatekeepers, filtering malicious traffic, blocking access to harmful sites, and inspecting content. This layer is your initial filter, but it is never your only one.
#3 Internal Protections: Building Interior Walls
Zero Trust is a rapidly growing strategy. The Zscaler ThreatLabz 2025 VPN Risk Report indicates that 81% of organizations have either adopted a Zero Trust model or are in the process of doing so. Additionally, companies with a Zero Trust architecture report an average of 42% fewer security incidents.
A breach at the perimeter shouldn’t grant keys to the kingdom. Network segmentation and strict access controls create internal barriers that contain lateral movement. Adopting a Zero Trust mindset: “never trust, always verify”, means authenticating and authorizing every request as if it originates from an open network. This limits an attacker’s reach, isolating them to a single segment.
#4 Endpoint Hardening: Securing Every Device
Every laptop, phone, and server is a potential entry point. Endpoint Detection and Response (EDR) solutions provide deep visibility into these devices, identifying suspicious behavior and enabling rapid investigation and response. Coupled with rigorous patch management policies, this layer ensures your devices are both hardened against attacks and closely monitored.
#5 Application Safeguards: Protecting the Crown Jewels
Data resides within applications, making this layer critical. Security must be integrated into the software development lifecycle (SDLC) through practices like static and dynamic application security testing (SAST/DAST). Encryption, both for data at rest and in transit, alongside robust API security, ensures that even if data is accessed, it remains unintelligible and useless to an attacker.
#6 Data Integrity & Recovery: Your Strategic Insurance Policy
Ransomware and data corruption are business-level threats. Your ability to recover defines your resilience. This layer is your guarantee. Automated, immutable, and air-gapped backups ensure a clean copy of critical data always exists. A regularly tested disaster recovery plan transforms those backups from a theoretical concept into a proven tool for business continuity.
#7 Mission Control: Policies, Monitoring & Response
This is the central nervous system that binds all other layers together. A Security Information and Event Management (SIEM) system aggregates logs from across your environment, providing a single pane of glass for threat detection. This technology is empowered by a formal, practiced Incident Response Plan (IRP) and clear, enforceable security policies. Without this layer, signals are missed, and responses are slow and chaotic.
From Silos to Strategy: Making Your Layers Work Together

These layers are not a checklist of isolated tools. Their true power is realized through integration. Consider this flow: a user clicks a phishing link (Layer 1), bypassing the perimeter (Layer 2). Malware attempts to execute on an endpoint (Layer 4), but the EDR tool detects and blocks it, simultaneously sending an alert to the SIEM (Layer 7). The security team, guided by their IRP, uses NAC policies (Layer 3) to quarantine the device, preventing any lateral movement toward sensitive data (Layer 5).
This orchestrated response is the ultimate goal. It’s what transforms a collection of security products into an intelligent, responsive organism.
How CMC Global Supports Businesses in Cybersecurity Framework Implementation
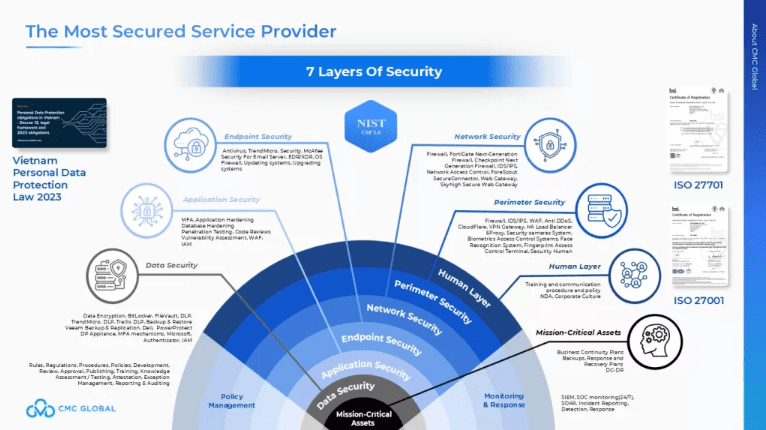
Businesses partnering with CMC Global benefit from a security-first approach that ensures compliance with industry standards. Through expert consulting services, CMC Global helps businesses navigate cybersecurity regulations like ISO 27001, ISO 27701, NIST CSF 2.0 with 7 layers of security: Human layer, Perimeter security, Network security, Endpoint security, Application security, Data security, Mission-critical assets.
Additionally, CMC Global fosters a highly skilled cybersecurity team, encouraging professionals to obtain top industry certifications such as Certified Information Systems Auditor (CISA), Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and Offensive Security Certified Professional (OSCP).
This commitment to compliance and expertise strengthens businesses’ security posture, mitigating risks and ensuring regulatory alignment.
Contact us today to learn more about how CMC Global can support your cybersecurity strategy!