While it serves as a crucial enabler for advancing their transformation agendas, research indicates that the cloud also brings significant cybersecurity risks, potentially threatening the integrity, confidentiality, and availability of banking services.
The essential cybersecurity strategies that Australian banks must adopt to safeguard their operations, protect customer data, and maintain the stability and security of the financial ecosystem will be present in this article.
Cybersecurity Threats to Cloud-Based Banking
Cloud-based banking has revolutionized the financial industry with its convenience and efficiency, but it has also opened new doors for cybercriminals, posing serious security risks. Recognizing these threats is essential for creating effective defenses.
#1 Data Breaches
The biggest risk for cloud-based banking is the threat of data breaches, especially given the recent surge in cyber intrusions in Australia’s BFSI sector. Notable incidents, such as the Medibank breach, highlight how cybercriminals exploit cloud vulnerabilities to access sensitive customer data, including personal details and transaction histories.
These breaches can lead to financial losses, identity theft, and a serious decline in customer trust.
#2 Phishing Attacks
Phishing remains a widespread tactic where attackers trick banking customers into revealing their login credentials by enticing customers to banking communications channels like emails, SMS, or fake websites. The cloud environment intensifies this threat by allowing attackers to conduct large-scale, sophisticated phishing campaigns that can simultaneously target millions of users. attackers obtain sensitive information, such as login credentials or account details, by masquerading as a trustworthy entity.

#3 Account Takeover (ATO) Attacks
Recent findings by digital fraud management firm Sift revealed a staggering 350% increase in Account Takeover (ATO) attacks in 2023, with 18% of respondents reporting at least one incident.
ATO fraud employs various tactics such as credential-stuffing, password-cracking tools, phishing, and social engineering. The scalability of cloud infrastructure is unintentionally allowing cybercriminals to automate and amplify their attacks against banking platforms.
#4 Distributed Denial of Service (DDoS) Attacks
DDoS attacks target cloud-based banking services by overwhelming them with excessive internet traffic, making them inaccessible to legitimate users. These disruptions not only disrupt operations but can also mask more malicious activities like data breaches or fraud.
#6 API Vulnerabilities
As cloud-based banking relies heavily on Application Programming Interfaces (APIs) for integration with other services, vulnerabilities in these APIs result in unauthorized access and data leaks.
#7 Cloud Misconfigurations
Misconfigured cloud settings are a leading cause of data exposure. Even minor errors in cloud storage permissions or security settings can inadvertently expose sensitive data to the public or cybercriminals.
Technology Practices Enhancing Cloud Security

This section discusses the essential best practices that can significantly enhance the cybersecurity posture of cloud-based banking platforms.
#1 Implement Strong Authentication Methods
One of the best defenses against unauthorized access is the use of robust authentication methods. Multi-factor authentication (MFA), which requires two or more verification steps, along with biometric authentication like fingerprint or facial recognition, adds essential layers of security.
#2 Data Encryption and Protection Strategies
Encrypting data both at rest and during transit ensures that even if unauthorized parties intercept or access it, the data remains unreadable and unusable. It’s crucial to use strong encryption standards and technologies to safeguard sensitive banking information.
#3 Secure Cloud Architecture and Isolation
Creating a secure cloud architecture that separates sensitive banking applications and data from less secure environments can greatly reduce the chances of breaches. Adopting a hybrid cloud approach, which combines public and private clouds, allows banks to better control critical operations and data.
#4 Regular Software Updates and Patch Management
Regularly updating all systems, applications, and infrastructure components with the latest security patches is essential for defending against known vulnerabilities. Automated patch management tools can help ensure these updates are applied promptly and efficiently.
#5 Access Control and Management
Enforcing strict access controls and management policies ensures that only authorized individuals can access sensitive banking systems and data. This includes applying the principle of least privilege, where users and internal departments are given only the minimum access or permissions necessary to do their jobs.
Proactive Practices Enhancing Cloud Security – Think like a CXO

#1 Adopt a holistic perspective on cyber risks
Consider cyber risk as broader risk issues, rather than viewing them as IT concerns within their IT departments. Some executives mistakenly believe that cyber risks can be handled through financial investments in IT solutions. Instead, it is important to manage cyber risks comprehensively within a risk-management framework.
Strengthening cybersecurity governance and fostering collaboration should be accompanied by a distinct risk-management framework that separates cyberrisks from other nonfinancial risks such as operational and technological risks.
#2 An Enterprise Risk Management (ERM) framework dedicated to addressing cyber risks
According to the 2023 CEO Survey by Gartner, Risk management is becoming a rising priority for FS (Financial services) CEOs, with the growth of 72% in comparison to the previous year.
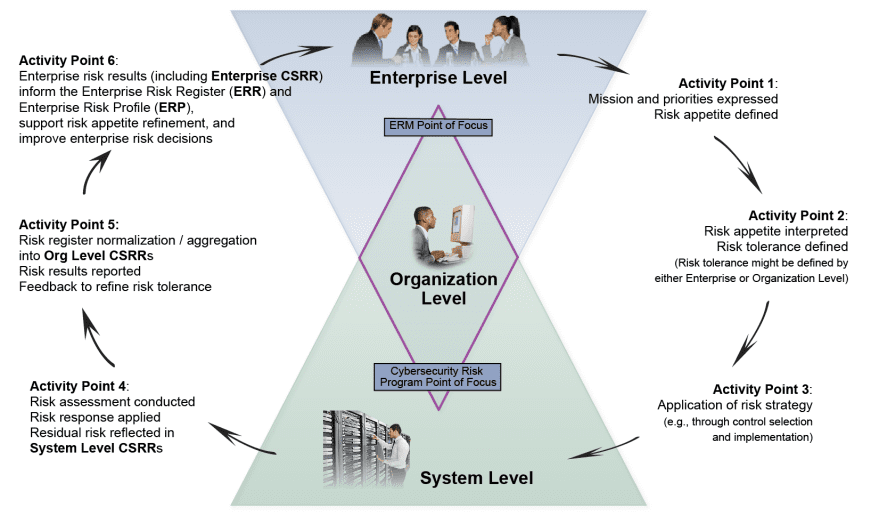
To comprehensively address cybe risks and enhance their cyber maturity, banks can consider adopting established international frameworks like the cybersecurity framework developed by the US National Institute of Standards and Technology (NIST) for planning and integrating an enterprise-wide process for integrating cybersecurity risk management information into enterprise risk management.
The Activity Points includes:
1 – Leaders define and record enterprise mission, priorities, and risk appetite. They also assign responsibility for managing both positive and negative risks.
2 – Organization-level managers interpret risk appetite into specific guidance regarding security and privacy requirements, and associated risk tolerance.
3 – Risk strategy and requirements aid implementation of shared security solutions and system level controls to achieve an acceptable level of risk, covering aspects like protection, detection, response, and recovery.
4 – Outcomes from risk responses are recorded as residual risks in system-level risk registers, which are continuously assessed and monitored.
5 – Risk registers are standardized and aggregated at the organizational unit level, supporting
reporting, analysis, and organization-level adjustment.
6 – The combined risk results across the organization are used to maintain an enterprise-level risk register and profile, which guides business decisions and any needed changes to the risk strategy.
Let CMC Global Guide Your Transformation Journey
As the financial landscape continues to evolve, the importance of adapting to digital technologies and ensuring robust cybersecurity cannot be overstated. Through CMC Global cutting-edge technology offerings, customized solutions, and a commitment to staying at the forefront of industry trends, CMC Global equips Thai banks with the tools and expertise needed to remain competitive and relevant in a rapidly changing financial environment.

Schedule a free consultation to discuss your digital transformation needs.




