The Boardroom’s Biggest Barrier to Global Expansion
For forward-thinking US companies, building a tech hub overseas is a powerful strategy to access elite talent and accelerate innovation. Yet, this strategic move is often stalled by a critical question in the boardroom: “How do we mitigate the data security and compliance risks?”
For the CISO, it’s a question of extending control. For the CTO, it’s about integrity of systems. For the CEO, it’s about protecting brand reputation. The concern is universal: an offshore team can feel like a black box, creating vulnerability and compliance gaps.
The solution isn’t to avoid global talent, it’s to change the paradigm. The goal is to move from an offshore vendor to a Best-Shore partner: an extension of your team that operates under a unified, rigorous, and demonstrable security framework. This framework shouldn’t be custom-built; it must be based on the proven, auditable standards you already trust.
The Blueprint: A 7-Layer Security Framework for the Modern Enterprise
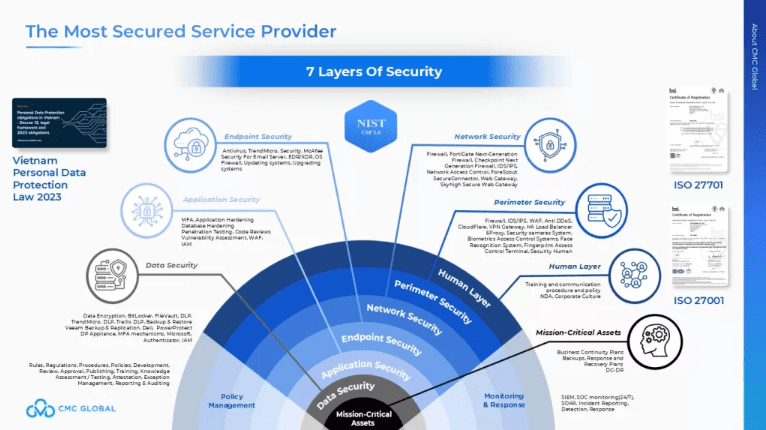
The most successful partnerships are built on a defense-in-depth security model. This multi-layered approach ensures that even if one layer is compromised, others stand firm. It’s this structure that provides the evidence needed for compliance audits, from SOC 2 to GDPR.
Here is the framework that leading best-shore partners employ to mitigate risk and ensure compliance:
#1 The Human Firewall: Your First Line of Defense
Technology is futile without the right people. Our first and most critical layer is building a culture of security. Every team member undergoes rigorous background checks, continuous GDPR and security training, and signs strict confidentiality agreements. We turn your offshore team into a proactive, security-conscious unit that identifies and mitigates human risk before it becomes a technical one.
#2 Perimeter Security: The Digital Gate
This is our first technical barrier. Think of it as a digitally fortified gate with multiple checkpoints. We employ enterprise-grade firewalls, Intrusion Prevention Systems (IPS), and advanced threat intelligence to monitor and block malicious traffic 24/7. This layer ensures that unauthorized entities cannot even get close to your data, keeping the external digital perimeter locked down.
#3 Internal Protections: Building Interior Walls
Should an attacker breach the perimeter; internal network segmentation acts as interior walls in a building. We isolate development, testing, and production environments and enforce strict controls on lateral movement within the network. This means that access to one system does not grant access to all, containing any potential breach to a minimized, controlled area.
#4 Endpoint Hardening: Securing Every Device
Every laptop, desktop, and server is a potential entry point. We eliminate this vulnerability through stringent endpoint management policies: enforced disk encryption, mandatory anti-virus/anti-malware software, regular patch management, and policies that prevent the use of unauthorized USB devices. Every device that touches your code is secured, managed, and monitored.
#5 Application Safeguards: Protecting the Crown Jewels
Your applications are where data lives. We embed security directly into the development lifecycle (DevSecOps). This includes mandatory code reviews, static and dynamic application security testing (SAST/DAST), and adherence to OWASP Top 10 principles. By building security in from the first line of code, we protect your most valuable assets at their core.
#6 Data Integrity & Recovery: Your Strategic Insurance Policy
GDPR mandates resilience and the ability to restore data availability quickly after an incident. Our robust, encrypted backup strategy is your insurance policy. Data is backed up regularly to secure, geographically disparate locations, ensuring we can meet strict Recovery Time and Point Objectives (RTO/RPO) and guarantee business continuity no matter what.
#7 Mission Control: Policies, Monitoring & Response
The top layer unifies everything with governance and proactive vigilance. This is our Mission Control, featuring a 24/7 Security Operations Center (SOC) that monitors for anomalies in real-time. It’s supported by comprehensive policies for Data Protection Impact Assessments (DPIAs), breach notification, and Data Subject Access Requests (DSARs)—all aligned with GDPR. We don’t just set defenses and walk away; we constantly watch, analyze, and stand ready to respond.
Demonstrating Excellence: A Commitment to International Standards

While a NIST-aligned framework provides a powerful foundation for technical security and risk management, a truly robust partner demonstrates a broader commitment to excellence through internationally recognized certifications. These certifications provide independent, auditable proof of mature processes and a culture of continuous improvement.
The most sophisticated partners will validate their capabilities through a multi-faceted approach:
- ISO 9001: Certification for Quality Management Systems. This demonstrates a commitment to consistent quality in processes and services, ensuring that operational excellence is baked into every project delivery, not just security protocols.
- ISO/IEC 27001: The Gold Standard for Information Security Management (ISMS). This certification is a critical third-party validation that an organization has systematically assessed risks and implemented a comprehensive suite of security controls to protect information assets. It is a universal signal of mature data security practices.
- SOC 2 Type II Compliance: While NIST provides a framework, SOC 2 reports offer tangible, auditor-verified evidence that a vendor’s security controls are not only in place but are operating effectively over a period of time. This is often the most requested report by US companies as it provides unparalleled transparency into operational security.
- Adherence to GDPR Principles: For any US company with global ambitions or European customers, a partner that has baked GDPR’s principles like data minimization, right to erasure, and lawful processing into their DNA is essential. This proactive approach future-proofs your operations against expanding data privacy regulations.
A partner that invests in these certifications signals more than just compliance; they signal a foundational dedication to quality, security, and operational integrity that transcends any single project or client requirement.
Turn Your Offshore Strategy from a Security Risk into a Competitive Advantage
For forward-thinking US companies, building a tech hub overseas is a powerful strategy to access elite talent and accelerate innovation. Yet, this strategic move is often stalled by a critical question in the boardroom: “How can we ensure our data is secure and compliant if our tech team is overseas?”
At CMC Global, we transform this perceived risk into your greatest strategic asset. Our multi-layered, defense-in-depth security framework does more than protect your data, it strengthens your overall security posture, providing a level of specialized focus, resilience, and compliance readiness that is challenging to build in-house.
The goal isn’t to find a vendor who says they are secure. It’s to partner with a team that can prove it.
Ready to move from concern to confidence? Let’s discuss how our secure offshore hub can become your competitive advantage.




